Featured

Mercury Systems
April 16, 2025

Vodcast
Delivering RF signal processing solutions to the edge with MOSAMercury Systems
August 30, 2022
Blogs & Podcasts

In military environments, seconds can be the difference between life or death and mission success or failure. A soldier in hostile territory needs their mobile system to rapidly process sensor data to accurately analyze threats and take action. Intelligent sensor systems using artificial intelligence (AI) to make automatic critical decisions without human intervention rely on […]
Jennifer KeenanMarch 14, 2019
Read More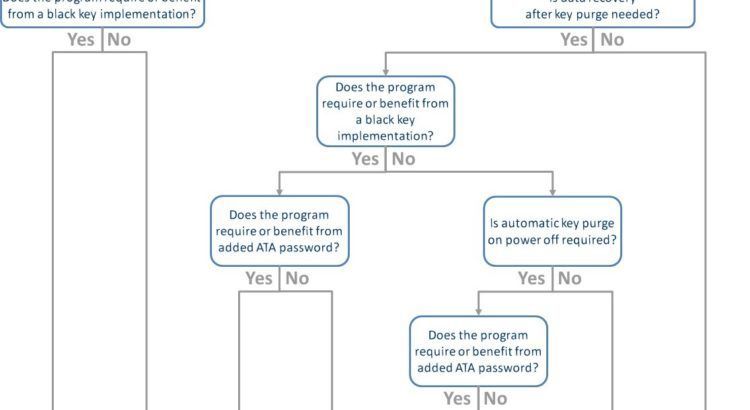
In my prior three posts, I provided an overview of encryption key fundamentals and the various encryption key mode strategies that can be implemented in a Mercury secure SSD. If you did not read those, stop everything and go back to them now!
Jennifer KeenanMarch 8, 2019
Read More
Cloud, Fog and Edge Computing for Defense Applications.
Shaza KhanMarch 5, 2019
Read More
Since the Wright Brothers first free-powered flight in 1903, air vehicles have relied upon discrete, analog sensors to supply the information required by their pilots. These sensors and their dashboard-clustered indicators may be regarded as the first and the analog approach to platform situational awareness.
John BrattonMarch 5, 2019
Read More



